About Friday?s Mass Hack Attack
The distressing emails started coming in on Friday, October 21st like SOS signals from a sinking ship.
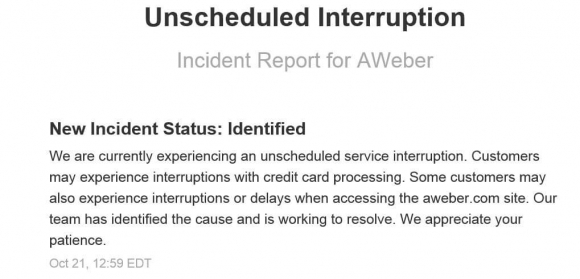
First, AWeber went down, stopping me from sending out newsletters and Trade Alerts.
Then Interactive Brokers crashed, making options price updates impossible.
Suddenly, Yahoo Mail wouldn?t take attachments.
Then Twitter went down.
Yikes!
What in the world was going on?
Was this a Soviet hack attack prior to a full scale nuclear strike?
Or was it the END OF THE WORLD?
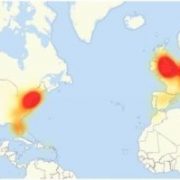
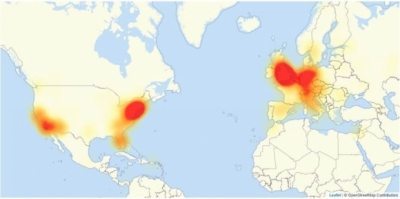
Cyber security firms were baffled over how quickly and widespread the attack became. Many thought that this was the biggest such attack in Internet history.
I asked one my friends at security giant, Palo Alto Networks (PANW), if it was the Russians again. He replied, ?You better hope it?s the Russians.?
The implication being that the Internet may have launched the attack itself.
What made this attack so damaging was that it was focused on a single company, Manchester, NH based Dyn, one of several companies that host the Domain Name System (DNS), essentially a switchboard for the Internet.
DNS is what allows computers to speak to each other. No DNS, no internet.
The other unusual aspect of this attack is that it was launched from millions of home appliances, like baby monitors, refrigerators and home security systems, instead of unsuspecting home computers.
It was a clever strategy because ?The Internet of Things? has invested far less money in cyber security.
Thus unleashed, these devices bombarded the Dyn website with millions of inquiries, causing it to grind to a halt in what is known as a ?distributed denial of service? (DDoS) attack.
Whether this was a Russian or Chinese attack in response to something the US government has done to them, or a prelude to a disruption of the US presidential election, is anyone?s guess.
The guys upstairs are till trying to figure it all out.
No less figures than Nobel Prize winner Dr. Stephen Hawking and Tesla?s Elon Musk have warned that computers and the Internet may have the power to pose a threat to human existence within a decade.
It all goes to show you how dependent our society has become on strings of ones and zeros lining up correctly, and how fragile that system is.
If the Internet goes down and stays down, millions would starve within months. No kidding!
It all shines a giant spotlight on one of my favorite long-term industries of the future, cyber security. Last week?s attack has just opened up a massive new market for them.
Instead of focusing on mainframes and servers, it now has to look at toasters.
Who?s really reading your email? I bet you?d like to know!
Another day, another hack attack.
There must be a way to make money out of this.
Wait! There is!
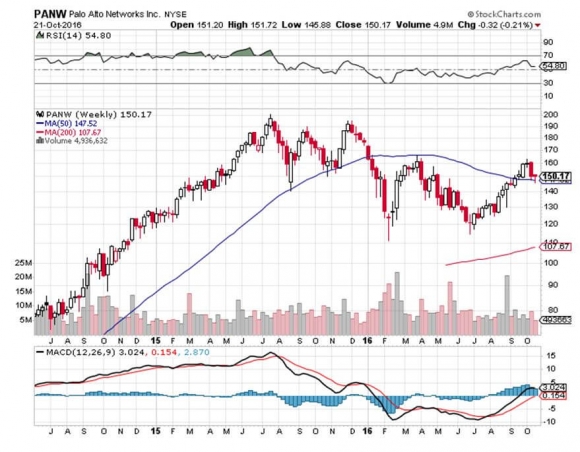
Palo Alto Networks is a San Francisco Bay Area cyber security company that offers companies and governments an innovative firewall platform solution for big, network-wide security problems.
In the P&L sweet spot they are.
I know the company well, and have been recommending to my subscribers that they buy the shares for the past year, during which time they tripled.
What? You want me to buy a stock that has just tripled?
Prospects for the firm are booming, with sales growth running at a torrid 30% YOY rate.
Yet, Palo Alto Networks has only 10% market share of an industry that is currently exploding. This is an aggressive, extremely well managed $15 billion company that is about to become a $150 billion company.
Keeping in contact with the Joint Chiefs of Staff on a weekly basis, I am constantly concerned at how serious the cyber security threat has become, yet how little understood it is by the public.
You don?t have to go any further than the management of Sony (SNE), one of the world?s largest multinationals, which was almost wiped out by hackers from one of the poorest and most backward countries in the world.
Upset by the take down of their leader, Kim Jong-un, in a low budget comedy, The Interview, North Korean hackers were able to bring the firm to its knees.
They downloaded the entire contents of Sony?s hard drives, leaking the juicy parts to online journalists (Angelina Jolie?s pay, etc.), and then wiped them clean, destroying some 3,000 computers and 8000 servers.
It was the hacking equivalent of a full-scale nuclear attack.
Sony had to revert to snail mail, couriers, and landline telephone calls to survive. They couldn?t even pay their employees. Some $6 billion in market capitalization was wiped out.
Now here is the scary part.
The FBI has confided in me that if the companies that comprise the S&P 500 were subjected to a Sony level attack, 90% are unlikely to survive. And the Sony attack was actually a primitive, simplistic, low-level attack.
A lot of countries don?t like the United States for any number of reasons. Now they can do something about it. That is a problem. And a market.
Palo Alto Networks maintains the world?s largest database of viruses and malware. That enabled it to trace the Sony attack to the Hermit Kingdom within hours.
It contained several lines of code that were identical to the ?Dark Soul? attack against South Korean banks in 2013 which incinerated 40,000 bank computers and caused $700 million worth of damage.
What the Sony attack revealed was a long history of massive under investment in cyber security by corporations and governments in the US, Europe, and Asia.
The potential future market for cyber security products and services is being wildly underestimated.
The great irony here is that the attack is not against systems, which are usually pretty secure. It is their human users that have become the problem.
Unfortunately, we are have become familiar with ?spoofing? emails where an innocuous email asks the user to ?click here? for an Adobe upgrade, a notice from Yahoo, or a request from PayPal to update your password.
Do so, and you invite lines of code that will eventually make it to your system administrator. Once they have his password, they can access or do anything.
Don?t think only dummies fall for this.
My friend, retired FBI chief Robert Mueller, had his personal account at the Bank of America cleaned out in a similar fashion. What was unusual in his case, they caught the transgressor, after a huge expenditure of bureau resources.
(Hint: if an incoming email appears the slightest bit suspicious, hover your mouse over the sender?s name, and the sending email address will appear. If it looks anything but belt and suspenders safe, don?t open it and mark it as SPAM. Especially watch for the last three letters of the address, which are always a tip off).
The FBI estimates that there are up to 10,000 hackers in the world with the capability of a Sony level attack, many operating from China, Russia, Eastern Europe, or other locations beyond the reach of US extradition treaties.
The global cyber war has been going on for about 15 years now, and the public hears very little of it.
In recent years, Iran attacked Saudi Arabia?s Aramco, destroying 30,000 computers, and briefly shutting down a portion of the country?s oil production.
A major attack was launched against the Venetian Hotel in Las Vegas which is owned by promin
ent Israel supporter and major Republican Party contributor, Sheldon Adleson.
There is a happy ending to this piece. You don?t need to place your entire wealth into gold bricks and bury them in the backyard to keep it safe.
If North Korea is a bicycle in the hacking arms race, the US is the F-35 Lightening next generation stealth fighter.
We are winning the cyber war hands down, but you?d never know it. This is a war fought silently, online, and in dark shadows.
President Obama in fact authorized a measured counter attack on North Korea?s information infrastructure, which proved devastating. But it was only a pinprick relative to what we could have done.
Our real cyber weapons are reserved for an actual shooting war sometime in the future. That?s to prevent the enemy from learning our true capabilities and preparing for them.
Imagine a country trying to defend itself with snail mail, couriers, and landline telephone calls from an American assault. Think the Sony attack times 10,000. Nothing would work.
It couldn?t be done.
Congress has so far refused to fund a substantial increase in America?s cyber warfare arsenal, preferring instead to spend money on old heavy metal weapons systems, like aircraft carriers, tanks, and the above mentioned F-35.
It?s all about sucking money out of Washington to create local jobs in red states to win elections. A stepped-up cyber program would focus money almost entirely on Silicon Valley.
Don?t want to do that!
This is how General George Armstrong Custer was sent to the Battle of the Little Big Horn with antiquated 16-year-old Civil War trapdoor Springfield carbines while the Sioux had state of the art Winchester ?yellow boy? repeaters.
And we know how that one turned out!
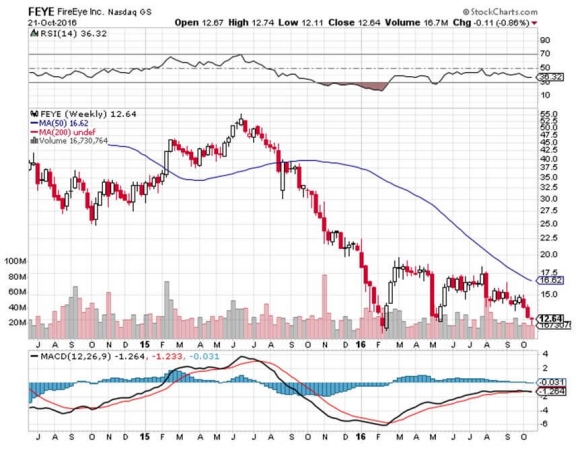
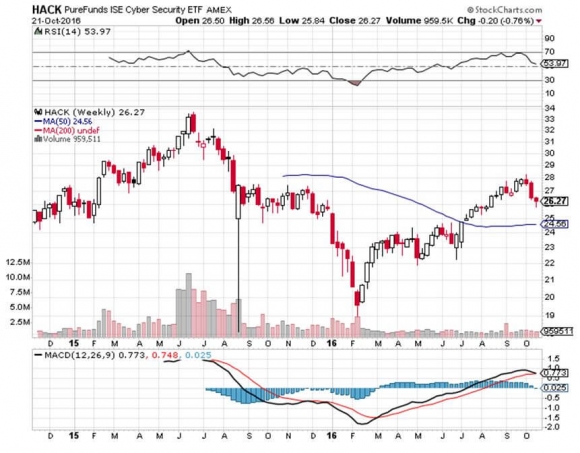
But don?t get mad. Get even. Take another look at Palo Alto Networks, FireEye (FEYE), and the Pure Funds ISE Cyber Security ETF (HACK).